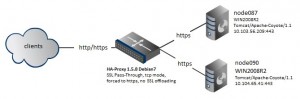
Scenario:
LOG:
root@frontend066:~# curl -k -L -I https://node087
HTTP/1.1 200 OK
Server: Apache-Coyote/1.1
Accept-Ranges: bytes
ETag: W/”6920-1395175166185″
Last-Modified: Tue, 18 Mar 2014 20:39:26 GMT
Content-Type: text/html
Content-Length: 6920
Date: Thu, 02 Apr 2015 19:52:00 GMT
root@frontend066:~# curl -k -L -I https://node090
HTTP/1.1 200 OK
Server: Apache-Coyote/1.1
Accept-Ranges: bytes
ETag: W/”6920-1397329391836″
Last-Modified: Sat, 12 Apr 2014 19:03:11 GMT
Content-Type: text/html
Content-Length: 6920
Date: Thu, 02 Apr 2015 19:53:12 GMT
root@frontend066:~# lsof -i tcp:443
lsof: no pwd entry for UID 109
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
lsof: no pwd entry for UID 109
haproxy 8927 109 4u IPv4 37796 0t0 TCP frontend066.bp.com:https (LISTEN)
curl -k https://frontend066.bp.com
curl -k https://10.104.65.109
HAProxy conf:
root@frontend066:~# cat /etc/haproxy/haproxy.cfg
global
log 127.0.0.1 local0
maxconn 4000
daemon
uid 109
gid 109
defaults
log global
timeout server 5s
timeout connect 5s
timeout client 5s
###REDIRECT 80 to 443 !must be http mode!
frontend http_to_https_redirect
bind :80
mode http
redirect scheme https if !{ ssl_fc }
frontend https_frontend
bind *:443
mode tcp
option tcplog
default_backend https_backend
backend https_backend
mode tcp
balance roundrobin
stick-table type ip size 200k expire 30m
stick on src
option ssl-hello-chk
server node087 10.103.56.209:443 check inter 2000 rise 2 fall 5
server node090 10.104.65.41:443 check inter 2000 rise 2 fall 5
listen stats :1936
balance
mode http
stats enable
stats scope http_to_https_redirect
stats scope https_frontend
stats scope https_backend
stats hide-version
stats realm Haproxy\ Statistics
stats uri /
stats auth gus:7Kn2zrgxwGw
stats auth bayil:zZFTGY1h/Lc
STATS:
http://10.104.65.109:1936